Friday, May 25, 2007
ACRONYM - Essentials of an effective team
Adequate planning
Balance of skills
Communication
Agreed standards
Monitoring skills
LAB CAM
ACRONYM - Success and failure of MIS
Analysis
Reduced levels of concentration
Knowledge of management information
Excessive management demands
Teamwork
Standards
MARKETS
ACRONYM - Factors to consider when planning for change
Attitude
Employment patterns
Re-skilling
Organisational structure
iAERO
ACRONYM - Corporate IT Security Policy
Discipline Procedures
Prevent Unauthorised Access
Check/detect Misuse
Monitor/Investigate Misuse
Establish Protection procedures (Backup)
DM
DP
UA
CM
MM
BP
ACRONYM - User Support
User manual
Newsletters
Help desks
On-screen help
Books
Bulletin board
FUN HOBB
ACRONYM - Threats to Information Systems
Hardware
Invalid data
Telecoms
Physical
Crime / misuse
System design failure
SHIT PCs
Monday, May 21, 2007
Thursday, May 17, 2007
Friday, May 11, 2007
Thursday, May 10, 2007
Intermediate Questions
a) Give 1 example of an information system that would be useful to managers at this level, and explain how they would use it. (3)
b) State the 2 other levels of task and/or personnel within an organisation (2)
2) The introduction or development of an information system will result in change that must be managed.
Describe 3 areas that will need effective management. (6)
3) Any personal data that an organisation holds on a computer about its employees, or it customers, is covered under the Data Protection legislation.
Describe 3 methods by which a company can ensure that the requirements of Data Protection legislation are followed. (6)
4) Management's understanding and involvment can play an important part in the introduction of a MIS.
Give 3 actions that managers could take to increase the chances of a MIS begin successful. For each action state how it would help ensure success (6)
5) There are a number of social, moral and ethical issues associated with the introduction and use of ICT systems. Some of these issues may possibly be covered in an organisations ICT code of practice.
Describe 4 issues that could affect an ICT professional (8)
6) Project Management and effective ICT teams
a) Explain why ICT projects are often sub-divided into tasks and allocated to teams (3)
b)Within ICT projects, describe the need for:
i) clear timescales (2)
ii) approval to proceed (2)
Tuesday, May 08, 2007
Friday, May 04, 2007
Thursday, May 03, 2007
Tuesday, April 24, 2007
User Support
- user manual
- telephone support
- on-site training
Products were often sold with support packages as extra, and these support packages were often as expensive as the product!
Nowadays there are more varied types of user support options:
- robotic support (Ikeas' Anna)
- chat/messenger based support
- animated user manuals
- FAQ/troubleshooting guides
- user forums
When considering what support you will provide for your users, you must deicded upon 3 things:
- effectiveness (how effective it is to help the users)
- the user experience (bad user experience may turn users off)
- cost
For example; Ikeas' robotic Anna is
- is fairly effective in answering simple questions about specific things, but not as good as a real person
- provides a good user experience because people are comfortable speaking to someone, but as good as a real person
- and less expensive than having rooms full of telephone support personel
Animated user manuals are better than text based manuals as users are more likely to use and understand them and therefore less likely to ring up telephone support (expensive!).
Thursday, March 29, 2007
Corporate IT security policy
- Prevent misuse
- Detect misuse through regular checking
- Investigate misuse through the use of monitoring software and audit trails
- Prevent unauthorised access
- Establish procedures for keeping data, for example, backup up data and maintaining passwords to limit access to files
- Lay down disciplinary procedures for breaches of security
Data is vital to organisations and companies. Any loss, theft or accidental disclosure could have catastrophic results. For example, a greenhouse salesman travelling around the country selling greenhouses would not want his list of customers or sales figures to be lost. The data would contain information about identifiable people and therefore contravene the DPA. Also, rival companies could steal his customers!
The Corporate IT security policy aims to:
- Make employees aware of their responsabilities with regards to data security
- Define an audit trail to record transactions
- To define how a company should comply with the current IT legislation
Wednesday, March 21, 2007
Legal Aspects
Adequate security is crutial to the success of an organisation. But threats can come from outside and from within. Remember Wibble that went mad and wanted to destroy all our databases using a virus? It happens a lot.
Check out the links:
An organisation needs to have a corporate IT security policy. Its aim would be:
- to prevent misuse from occurring
- to enable any misuse that did occur to be detected and investigated
- to lay down procedures that should prevent misuse
- to establish disciplinary procedures to be used when an employee has been found committing an act of misuse.
An organisation has a responsability to ensure that all its employees are aware of laws relating to IT and their responsabilities under these laws, in particular:
- Data Protection Acts 1984 and 1998
- Computer Misuse Act 1990
- Copyright Designs and Patent Act 1988
- Health and Safety at Work Act 1974
- EU Health and Safety Directive 87/391
Monday, March 19, 2007
Ethical Issues in IT
An unethical decision is not necessarily illegal. But in business, people justify unethical decisions by saying it is a 'dog-eat-dog' world.
A second-hand car salesman with a ropey old banger might make the decision to tell a nieve young lady interested in it:
 He made the decision to tell an un-truth in order to sell the banger. Not illegal, but unethical.
He made the decision to tell an un-truth in order to sell the banger. Not illegal, but unethical.
Unethical parts of Tom's day:
- Choice of password - easy to guess
- Reading personal email (for a long time!)
- Downloading photos
- Opening SPAM emails from unknown source - opening company network to attack
- Fails to log off - computer vulnerable to use by unathorised users
- Installing a game on company computers
- Disclosing password
- Downloading and storing pornographic images
Some of Tom's activities are illegal, others simply show poor conduct which are unethical when a company is paying Tom to work.
In order to be a doctor, you must sign the 'Hypocratic oath' which states that thay must not divulge personal information. If they do, they will be struck off.
IT professionals can join the British Computer Society (BCS).
Being a member of the BCS means that employers know that you will follow the code of practice.
Contractor UK is the professional body for IT contractors - not that they managed to stop IR35!
Employers may write 'codes of conduct' for their employees. This will outline:
- Responsabilities
- Authorisation
- Security
- Penalties
Tuesday, March 13, 2007
Rules to project success
- Good project management (using Gannt, project plans etc.)
- Appropriate and reasonable timescales
- Realistic client objectives
- Adherence to coding and design standards
- High priority given to thorough testing
- Use experienced/qualified team members (often more expensive)
- Thorough analysis and feasibility studies
- High levels of professionalism
- Appropriate, well managed roll-out procedure
- Involve end-users throughout process
Thursday, March 08, 2007
Project Managers problems

- analysing user requirements
- designing and prototyping
- writing and testing
- acceptance testnig
- installing and testing

Each phase requires their own specific skills and matched to specific team members.
- Team leaders
- Developers
- System analysts
- Consultants
- Testing and Q&A
A project manager has to consider the following problems:
- Costing
- Team members and skills
- Planning and timescales
- Monitoring and feedback
Monday, March 05, 2007
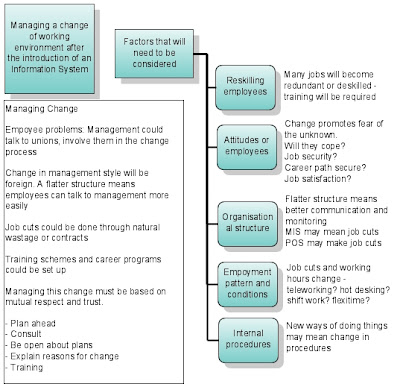
Organisational Structure - Managing Change
- Understand that the introduction of an information system will result in change – this must be managed.
- Eg.
BT restructuring
Supermarkets from 1970’s and nowadays
Factors to consider when planning for change: - Re-skilling employees
This may mean an employee doing more tasks than they did previously, and having to use ICT
A receptionist to a middle manager lucky enough to save his/her job in a reshuffle may find that they become a personal assistant to many managers requiring, significant ICT skills such as Outlook and email
- Attitudes of employees
Change causes fear and resistance
Fear they can’t do it
Fear they are going to be phased out of a job as their job becomes more menial (eg. car workers being replaced by robots with operators)
Centralised information means other departments can access information without needing to contact other departments directly
Job regarding can restrict an employees ambitions
Job satisfaction can be reduced and therefore their motivation
Information systems often reduce the need for social interaction
- Organisational structure
Better information across an organisation reduces the need for middle management and therefore flattens the structure
An MIS makes it easy for strategic management to monitor operations more efficiently and effectively, resulting in better planning and spotting problems sooner
Many decisions will be made automatically further reducing need for layers of staff (eg. automatic stock re-ordering)
- Employment pattern and conditions
Many jobs may be lost through redundancy (eg. robots at car plant)
Times of employment may change to shifts to maintain 24 hour working
Teleworking may mean more people working from home
- Internal procedures
The way things are done will change
Monday, February 26, 2007
Organisational Structure
- Division of labour
- Organisational structure chart
- Span of control
- Chain of command
- Pyramid or Hierarchical structure
- Horizontal or Flat structure
- Organisation structure levels