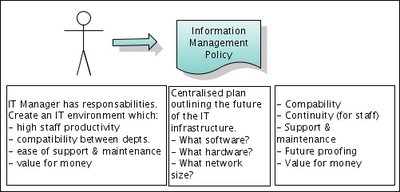
The responsabilities of an IT manager are:
The responsabilities of an IT manager are:
- To promote high productivity of staff
- To ensure compatibility and ease of communication between departments and clients
- To ensure ease of support and maintenance
- To ensure all decisions are good value for money
So these responsabilities effect every decision that is made concerning the IT environment.
When developing an Information Management Strategy, an IT manager must make decisions on software, hardware and configuration choices.
Each choice has costs and benefits which must be considered alongside the immediate, and long term requirements of the organisation/company.

When considering SOFTWARE choices for the organisation:
"Off-the-shelf"
- Known functionality
- Proven technology
- Known costs
"Bespoke"
- Exactly what is required therefore can improve staff productivity
- Future proofing can be built in providing potential value for money
Standardise on interface:
- Ease of support
- Ease of compatibility between users
When considering choices for HARDWARE:
Type of workstations
- Identical workstations = easy maintenance and support
- A complete roll-out = too expensive so rolls out in stages throughout the year
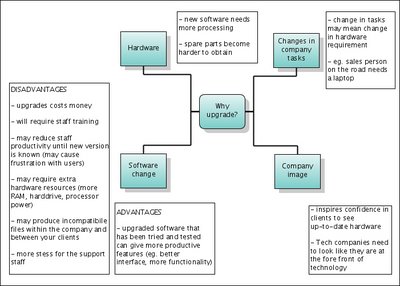
Upgrading considerations:
- Software - improvements in functionality and ease of use
- Hardware - more speed, less likely to get spares
- Ethos - looks good to clients if the company has new PC's
- Task driven - maybe your sales force needs internet access on the road = laptop
Should you upgrade to the latest version?
Yes!
- Extra features for your users means they will work more efficiently
No!
- Time and cost of re-training
- Until training, users may not be able to use the new functions and be less productive
- More hardware resources needed
- May not have all previous functionality
- Potentially imcompatible file types
- Staged roll-outs may make different departments incompatible
- More complicated support needed for different versions
Should emulation (a piece of software or hardware that allows a computer to pretend to be another type) be considered?:
Yes!
- Can run legacy software - short term incompatibility upgrade fix
- Enables different departments running different h/w and s/w to communicate
- More software can be run on a h/w platform
No!
- Extra program running = more resources needed (or runs slower)
- Will not exploit new features of the hardware
- May not exploit full features of software being run